Understanding End-to-End Encryption: A Comprehensive Overview
Written on
Chapter 1: Introduction to End-to-End Encryption
In recent times, many chat applications have implemented a robust security feature known as end-to-end encryption to protect your messages. This technology ensures that your communications remain confidential. But how does this encryption function, and what makes it distinctive? Let’s delve into the details of end-to-end encryption and its implications.
Section 1.1: What is End-to-End Encryption?
End-to-end encryption gets its name from the way it operates. When you send a message through a chat application, it is encrypted on your device using a specific key. This encrypted message travels securely over the internet and is only decrypted on the recipient's device with a corresponding decryption key.
"This means that only the sender and the intended recipient can read the messages, ensuring privacy."
Section 1.2: How End-to-End Encryption Works
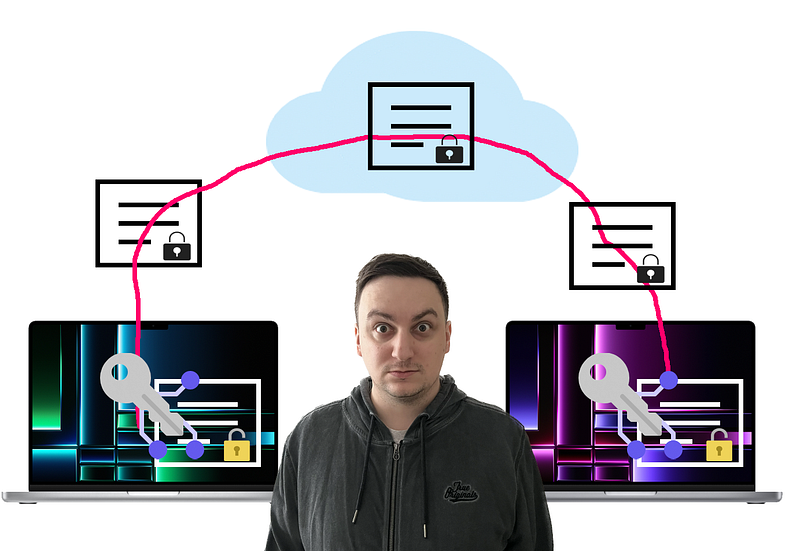
The encryption and decryption process is facilitated by the chat application itself, making it impossible for third parties to intercept and read the messages while they are being transmitted. However, it’s important to note that the messages remain decrypted on both the sender's and recipient's devices. If an unauthorized user gains access to either device, they could potentially read the messages stored there. Fortunately, iOS devices typically offer strong security features, making them less vulnerable than some Android devices.
Section 1.3: What Gets Encrypted?
When you send a message using an application that supports end-to-end encryption, both the text and any accompanying images are encrypted. This ensures that all parts of your communication are secure.
"Once received, the message is decrypted on the recipient’s device, allowing them to read it privately."
Chapter 2: The Role of Apps in End-to-End Encryption
Video Description: This video by BBC News discusses what end-to-end encryption is and how it functions to keep your messages secure.
When it comes to messaging applications, many, such as iMessage and WhatsApp, utilize end-to-end encryption. WhatsApp prominently displays a notification about this feature in every conversation, while iMessage quietly employs it without overtly advertising. For Facebook Messenger, users can opt into an encrypted mode by selecting “Go to Secret Conversation” in the chat settings.
"Other applications like Threema also offer end-to-end encrypted messaging and calls."
Section 2.1: The Impact of Encryption on Device Performance
While end-to-end encryption is crucial for safeguarding communications, it does require some computational resources. While most modern devices, such as iPhones or iPads, can handle this without issue, users may notice a slight decrease in battery life due to the additional processing required for encryption and decryption tasks.
Section 2.2: Conclusion
In summary, understanding end-to-end encryption is vital for anyone who values privacy in their digital communications. It ensures that your messages remain confidential and inaccessible to unauthorized entities. If you enjoyed this exploration into the world of encryption, please consider supporting my work!
Video Description: This YouTube video explains what end-to-end encryption is and its significance in modern communication.